Key Takeaways
- SOC 2 compliance is a framework that guides businesses on how to protect sensitive customer data such as addresses, credit card information, and other personal information.
- Non-compliance is not illegal. However, clients or customers are typically hesitant to partner/purchase from a non-compliant entity.
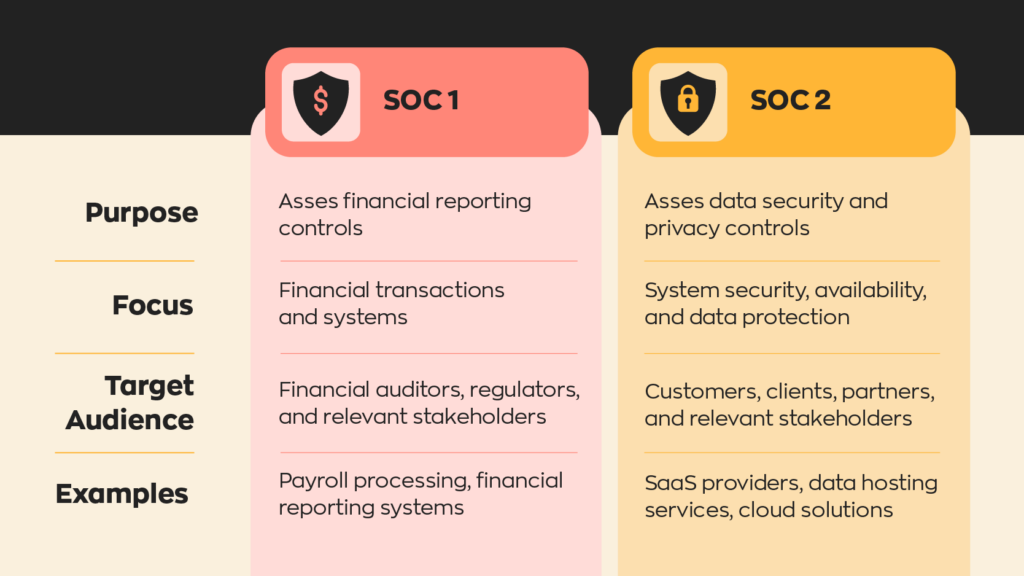
- The framework is built on five key factors defined by the American Institute of Certified Public Accountants: Security, availability, processing integrity, confidentiality, and privacy.
- A third party must measure SOC 2 compliance.
The world as we know it changed with the introduction of cloud-based software. Services like Google Drive, Dropbox, and various business solutions allow users to store their information remotely. This allows them to access their information no matter where they are. While this has enormous benefits, the flip side is cloud storage also introduces several unavoidable security issues. In theory, cloud-based systems are more vulnerable to outside attacks.
Data is valuable, which is why SOC 2 (Service Organization Control Type 2) compliance is so important. It ensures that customer data remains as safe as reasonably possible.
But what is SOC 2 compliance? How do you know whether your business is SOC 2 compliant? And, more importantly: what are the ramifications of not complying with the SOC 2 framework?
There’s a lot to go over today, so let’s dig right in!
What is SOC 2 compliance?
Before understanding SOC 2 compliance, you need a basic understanding of cloud technology. If you’re reading this, you probably know what it is already, so we’ll keep things simple.
Before cloud technology, computers required a physical connection to memory in order to access files. After cloud technology, files and data can be stored off-site and accessed remotely. For SaaS, this means businesses can use cloud-based software from anywhere, so long as they have an internet connection. In the long run, this saves businesses thousands, or even tens of thousands, of dollars.
However, as we mentioned above, remote access introduces some unavoidable vulnerabilities. It’s common for businesses to store customer information, such as addresses, zip codes, and even credit card information.
This is where SOC 2 compliance comes into play. SOC 2 itself is a security framework that businesses adhere to in order to keep customer information safe.
Why is SOC 2 compliance so important?
It’s pretty easy to see the risks of credit card information getting into the wrong hands, but other forms of data are also valuable. There’s evidence of this in recent history. Microsoft’s acquisition of LinkedIn in 2016 was largely spurred on by its vast amount of user data.
However, every piece of data has an individual behind it, and that individual has a right to privacy. So SOC 2 compliance isn’t just about protecting sensitive information. It also plays a critical role in maintaining customer privacy.
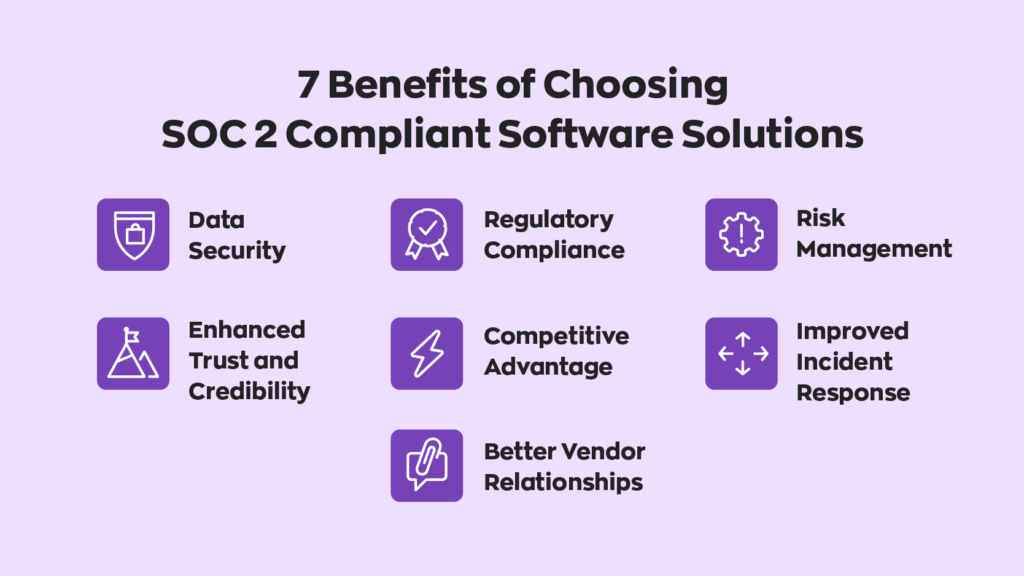
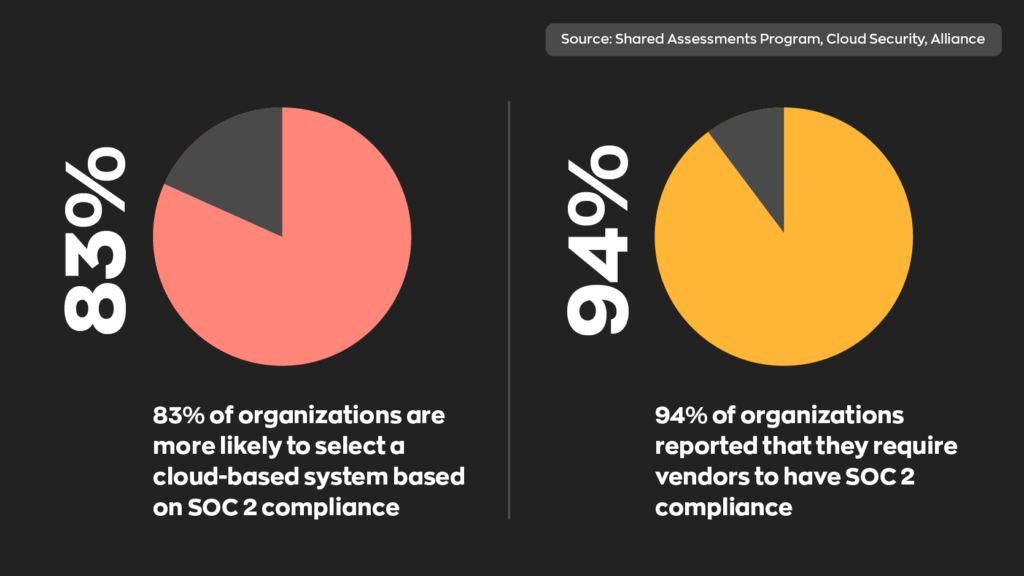
To be clear, not complying is perfectly legal. However, customers see compliance as a sign of trust between themselves and a business. If that business isn’t SOC 2 compliant, there’s a good chance that potential customers might look elsewhere. That trust is important, considering the sensitive data that businesses regularly collect. In short, not being SOC 2 compliant won’t bring legal ramifications, but it could push customers away to a more secure competitor.
For example, inFlow’s inventory system collects a large amount of customer data, and we take our duty to protect that data very seriously. That trust allows us to connect with businesses on a more personal level– and protect them in the process. This is why we ensured that inFlow is SOC 2 compliant, so our customers can have peace of mind.
Trust service criteria
SOC 2 compliance criteria are based on five trust service criteria defined by the American Institute of Certified Public Accountants (AICPA). These five criteria are as follows: Security, availability, processing integrity, confidentiality, and privacy. While some may seem to overlap (like confidentiality and privacy), each is distinct in the context of SOC 2 framework. Each of these criteria has its own criteria, or “focus” points, in order to be SOC 2 compliant.
Security
This refers to a business’s ability to protect information from vulnerabilities and prevent unauthorized individuals from accessing or disclosing private information. Unlike the other four criteria, security is mandatory.
Availability
Availability is, for the most part, exactly what it sounds like. It’s meant to ensure that the relevant systems and information are available to the user whenever necessary.

Processing integrity
This refers to whether or not a system works as intended. An important note here is that this is different from data integrity. A system can still work properly when it receives the wrong data. For example, if a customer enters a fake name, that’s faulty data. But as long as the package arrives at the correct address, the system is working correctly.
Confidentiality
This one is what most people probably immediately think about when it comes to SOC 2 compliance. Confidentiality refers to how an organization protects confidential information. This can be by limiting access, controlling where it’s stored, or by moderating its usage. This typically defines what employees can or cannot access certain information.
Privacy
This refers to how a business protects its customer’s personally identifiable information or PII. Depending on the business or organization, PII can refer to many different things. Including but not limited to: ethnicity, gender, sexuality, and sometimes individual health.
What should you look for in a SOC 2 compliant partner?
Of course, just being SOC 2 compliant doesn’t mean a business is automatically trustworthy. You’ll have to look a bit deeper in order to decide whether they’re a viable business partner. We haven’t touched on this yet, but SOC 2 is also an auditing process, meaning a certified auditor inspects the system and decides whether or not it meets the standards.
However, something important to look for is that a business has been audited by an impartial third party. Mostly because it’s a little silly to say “we investigated ourselves and found nothing wrong..”
Once the auditor completes the SOC 2 compliance process, they then create an SOC 2 report. These tend to be long and full of information, so here are some things to look out for.
- Report date – the audit report should be current and up to date – within reason.
- Description of services and the relevant systems.
- Any exceptions to compliance. Sometimes, things happen, but you should note and examine any egregious exceptions with caution.
- The auditor’s assessment which may be any of the following:
- Unqualified (Clean) – This is the ideal outcome and indicates the organization is adhering to SOC 2 compliance.
- Qualified – Minor errors may exist, but overall, statements are accurate.
- Adverse – Significant mistakes exist; therefore, the organization is not considered SOC 2 compliant.
- Disclaimer – There is insufficient evidence to form an opinion.
SOC 2 Type I vs SOC 2 Type II Assessments
When your organization decides on a SOC 2 assessment, it can choose from either a SOC 2 Type I or a SOC 2 Type II assessment. The SOC 2 Type I assesses the design and controls at a specific point in time. SOC 2 Type II assesses both the design and operating effectiveness over a defined audit period, usually 6-12 months.
inFlow has passed SOC 2 compliance
Our inventory management software inFlow is entirely cloud-based, and we understand that many of our customers may feel less secure because of this. So, to prove to our customers that we are dedicated to keeping their data safe, we underwent the necessary steps to make inFlow SOC 2 compliant!
Our cloud-based inventory software allows you to access our system from anywhere, setup multiple locations, and take advantage of our mobile app. All while knowing that all of your sensitive data is safe and secure.






0 Comments